B-2 vs Iranian Air Defense: Genuine Game Changer or Expensive PR Stunt [i]
Did the B-2 genuinely change the game in Iran and bring peace through force, or was it just a masterfully orchestrated PR stunt?
The B-2 bomber is a well-known yet still enigmatic aircraft that continues to capture the imagination of the aviation world, particularly among those who view it as a game-changer capable of projecting U.S. military power, or simply strength through presence, anywhere on the globe.
Several excellent books discuss the development of the B-2 in detail; therefore, this article will not revisit that history. Instead, key titles will be listed in the references. The purpose of this piece is to evaluate the B-2 Spirit in the context of modern air defense systems. Is this iconic aircraft truly a game-changer? Can it dominate the skies and remain invincible, or is it perhaps just one of several masterpieces born from the marriage of the Pentagon, the Military-Industrial Complex, and Hollywood & Mainstream Media?
Background
The B-2 Spirit was conceived during the height of the Cold War, a period defined by the nuclear arms race and the doctrine of mutually assured destruction. The U.S. needed a strategic bomber that could penetrate deep into Soviet airspace, deliver nuclear weapons, and evade detection by increasingly advanced radar systems. Existing bombers, such as the B-52, were large, fast, and capable, but they were also vulnerable to sophisticated surface-to-air missile systems and interceptor aircraft.
The B-2 was designed to ensure credible second-strike capability—the ability to retaliate after a nuclear attack, which is the cornerstone of deterrence. It needed to reach highly defended targets in the Soviet Union without relying on fighter escort or electronic jamming from other aircraft.
At the heart of the B-2 Spirit's revolutionary stealth technology lies the work of a Soviet physicist, Professor Petr Ufimtsev. While he did not design the aircraft, his mathematical theories on electromagnetic wave reflection provided the essential foundation for making stealth aircraft a reality. In the 1960s, Ufimtsev published a paper titled "Method of Edge Waves in the Physical Theory of Diffraction", which detailed how radar waves interact with various surfaces and edges.
His work was largely overlooked in the Soviet Union, but translated and declassified by the U.S. Air Force, it became a cornerstone for American stealth research. Ufimtsev had essentially shown that radar cross-section (RCS) could be mathematically predicted—and therefore manipulated or minimized.
American engineers, particularly those at Lockheed’s Skunk Works and later at Northrop Grumman, utilized Ufimtsev’s mathematical models to design aircraft with shapes that deflect radar waves away from the emitter, rather than back toward it. This led to the creation of the F-117 Nighthawk, the world’s first operational stealth aircraft, and later the more aerodynamically refined B-2 Spirit.
The B-2's smooth, blended flying wing shape owes much to the insights derived from Ufimtsev’s calculations. Its surface curvature, edge angles, and material coatings were all optimized using computational applications of his diffraction theory. Without Ufimtsev’s theoretical framework, the advanced stealth shaping of the B-2 would not have been possible.
Famous Stealthiness
Is the B-2 Spirit Really Stealthy and “Invisible” to Radar?
The answer is not straightforward. The B-2 Spirit exhibits remarkably low observability characteristics, particularly in its ability to evade detection and tracking by modern air defense radars. However, it is not truly “invisible.”
The key lies in how the aircraft interacts with radar systems: the B-2 doesn’t appear on radar as a typical aircraft. Instead, it appears as an anomalous return, often interpreted by radar operators as background noise or interference, and thus filtered out by automated radar processing systems.
The B-2’s shape, structure, and coating were optimized to minimize its radar cross-section (RCS), especially against fire-control radars used by the Soviet Union. These radars typically operate in the centimeter-wave (X- and Ku-band) range, which is ideal for guiding missiles to targets. Against these, the B-2 performs exceptionally well.
However, less attention was given to older surveillance and early warning radars, especially those operating in metric wavelengths (VHF and UHF bands). These longer-wavelength systems, though considered obsolete by many Western standards, have characteristics that can detect stealth aircraft, albeit with low resolution. In particular, the large size of the B-2 can result in resonant scattering effects in these bands, making detection possible under the right conditions.
The Soviet Union, and later Russia and other nations, conducted extensive research into the B-2’s radar visibility. This included simulations, scale model testing, and radar cross-section (RCS) measurements across a wide range of frequency bands. While most of the findings remain classified, some results have appeared in technical literature and academic publications, offering a glimpse into the B-2’s detectability.
Ultimately, the B-2’s stealth is a dynamic capability, highly effective against certain systems, but potentially vulnerable to others, especially when those systems are designed or adapted to defeat stealth platforms.
The cat-and-mouse game of radar measures and countermeasures continues. Stealth technology evolves, and so do detection techniques. In this ever-changing landscape, no aircraft is truly invisible, only harder to find.
“Unlock the Stealth Code”
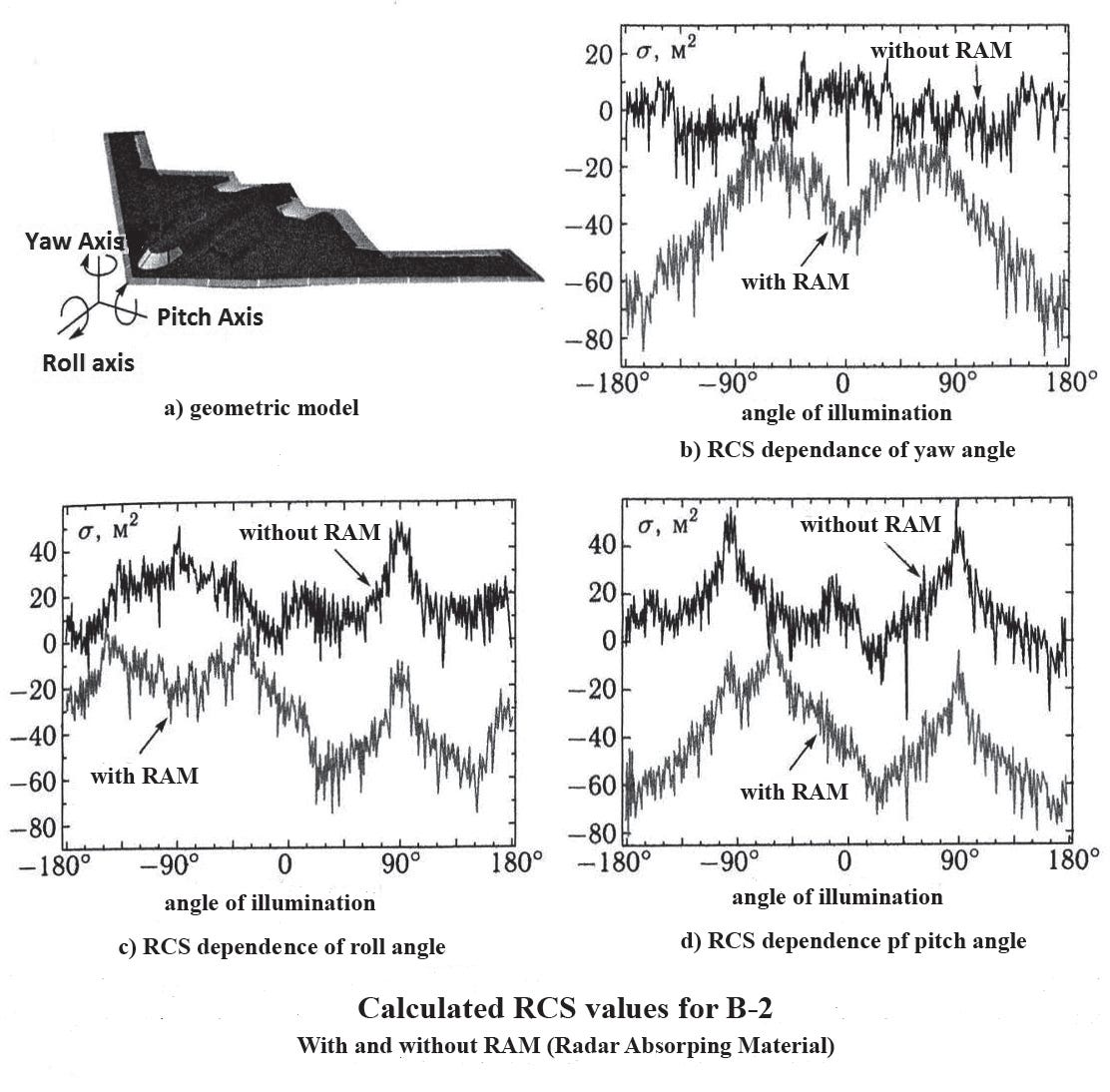
To analyze the radar scattering characteristics—specifically the Radar Cross Section (RCS)—the basic step is to make a simplified geometric model:
In a book by I. Sukharevsky1, in the modeling process, the aircraft's smooth surfaces were approximated using 26 triaxial ellipsoidal sections, while 24 straight-edge scattering elements were used to represent surface discontinuities and angular features. These simplified shapes allowed for effective simulation of the aircraft's radar scattering behavior across various frequency bands. It is essential to note that for serious military analysis, these models for analytical purposes will be significantly more complex.
For the realistic simulation, such as Ansys HFCC, Electrodynamics, Altair FEKO, MATLAB & Simulink, to mention just a few, the model's surface shall incorporate a Reflection Absorption Coating (RAC) of the Sommerfeld type, which mimics certain properties of actual Radar Absorbent Materials (RAM) used on stealth aircraft.
The greatest effort in reducing the RCS is focused on the forward aspects of the aircraft. However, there are greater returns to be had for other aspects, or at least for some angles. These trade-offs promise some advantages over well-designed bistatic radar networks. Secondly, though shaping is the first principle in reducing RCS and must be carefully considered in the design of low-observables, long wavelengths are less affected by the shape of the airframe and its details.



B-2 in Combat
B-2 First Combat - Aggression against Yugoslavia
From the Air and Space Forces2 :
…” Exactly 51 pilots flew the B-2 in combat. Most of them flew one mission; a handful flew two, and one pilot flew three times. The B-2 mission-capable rate during Allied Force, not counting low-observable maintenance, averaged about 75 percent. When such maintenance is included, the figure is about 60 percent. However, not a single B-2 mission started late, and only one airplane had to abort its mission for an in-flight mechanical problem. Each B-2 could—and, in some cases, did—attack 16 targets in 16 different locations per mission. Pilots reported they were apparently never detected…”
Reading that article is like reading pure marketing material written at the level of a salesperson trying to sell used equipment to a hamburger-loving customer. The biggest lie is that B-2 was never detected.
Also, the Serbian side knew the B-2’s radar scattering characteristics (the author worked on that).
The B-2 actions against the Federal Republic of Yugoslavia will be addressed in a separate article.
Against the Taliban
During the early 2000s, some of the most straightforward missions for U.S. B-2 Spirit bomber crews were conducted over Afghanistan, targeting Taliban positions. These operations, though logistically complex, presented minimal combat risk. The Taliban lacked radar systems, surface-to-air missiles, or interceptors, making it virtually impossible for them to detect—let alone counter—the stealth bombers flying high above.
For B-2 crews, the missions were considered routine in tactical terms, with the greatest challenge being the duration of the flights. Bombers often flew nonstop from the continental United States, requiring aerial refueling and round-trip sorties lasting more than 40 hours. Despite the physical and mental strain of such long missions, the absence of enemy air defenses made these deployments among the safest and most predictable in the B-2’s combat history.
The practice for Iran: bombing Houthis in Yemen
In a show of strategic airpower and a clear message to Iran, on 17 October 2024, the US deployed a B-2 to carry out a precision strike against Houthi military infrastructure in Yemen. Compared to Afghanistan raids, the Houthi militia has technology that can put a B-2 in harm’s way if they can establish a lock. For that reason, the whole flight path was swiped with EW and SEAD aircraft prior to a B-2 arrival.
The B-2s, which flew from Whiteman Air Force Base in Missouri and conducted aerial refueling en route, struck a hardened command-and-control facility near Sa’dah, believed to be central to coordinating Houthi attacks on shipping lanes and Saudi territory. The target was chosen for its strategic value and the difficulty of reaching it with conventional aircraft due to dense air defense coverage and rugged terrain.
Defense analysts noted that the use of the stealth bomber, capable of delivering bunker-busting precision munitions while remaining virtually undetectable, sent a clear message about U.S. resolve without escalating to a wider ground conflict.
Pentagon officials emphasized that the mission was surgical and proportional, aimed at degrading Houthi operational capacity rather than expanding the scope of the conflict. No civilian casualties were reported, and post-strike assessments indicated a high level of accuracy and mission success (if US reports are to be believed).
“Shaping Operation” - Israel’s Attack on the Iranian Air Defense
At the onset of the recent Israel-Iran conflict, Israel initiated a highly coordinated, multi-layered air campaign aimed at systematically degrading and neutralizing Iran’s air defense network within the first few days. The operation integrated cyber warfare, electronic warfare, long-range precision strikes, and, most critically, the use of a fifth column. This internal element carried out targeted assaults on key Iranian positions using remotely operated drones and Spike anti-tank guided missiles, disrupting defenses from within. These pre-placed operatives and concealed assets struck radar nodes, communication hubs, and mobile SAM units, creating localized chaos and confusion. Following these preliminary attacks, Israel's stealth assets, particularly F-35I “Adir” aircraft, penetrated Iranian airspace in a tightly synchronized offensive designed to blind radar coverage, suppress missile batteries, and paralyze the core of Iran’s command-and-control architecture.
The use of covert elements embedded within Iranian society was part of a carefully orchestrated operation. In several cases, drone assembly and launch sites were reportedly established in close proximity to Islamic Revolutionary Guard Corps (IRGC) facilities, sometimes even within the same neighborhoods. This level of access and operational freedom highlights the extent to which Mossad and Israeli intelligence had succeeded in penetrating Iranian society and its security apparatus. The ability to stage, arm, and remotely deploy drones and guided munitions from within Iran’s own borders suggests not only detailed intelligence but also deep infiltration and long-term planning.
The operation began with cyber attacks targeting key nodes in Iran's air defense communication and radar systems. These cyber intrusions—likely developed over years—were used to introduce malicious code into networked radar installations and command centers, causing confusion, data corruption, or complete shutdown of systems. This was followed by electronic warfare operations, where Israeli aircraft, particularly specialized platforms like the Gulfstream G550 Nachshon Shavit and Eitam, jammed radar frequencies and disrupted communications. These aircraft operated from standoff distances and coordinated their jamming to coincide with kinetic strikes.
Simultaneously, Israel deployed its F-35I “Adir” stealth fighters to penetrate Iranian airspace undetected. Operating alongside F-16 and F-15 strike aircraft, the mission focused on eliminating strategic air defense targets, including SA-17, SA-15, and Khordad-3 surface-to-air missile systems, as well as early warning radar installations, especially in the western part of the country. The F-35Is, leveraging their stealth capabilities, were able to fly deeper into Iranian territory, employing terrain masking and low-observable flight profiles to avoid detection by the remaining elements of Iran’s integrated air defense. These aircraft delivered precision-guided munitions with high accuracy, significantly degrading Iran’s ability to track, target, and engage incoming threats.
The Israeli Air Force also used long-range munitions such as Delilah cruise missiles, Rampage air-to-ground missiles, and Harop loitering munitions to destroy SAM sites, power relays, and radar installations. Some of these were launched from beyond Iranian borders, particularly from aircraft operating in Iraqi and Syrian airspace or international airspace over the Persian Gulf, minimizing risk to Israeli assets while maintaining offensive pressure.
A particularly effective component of the campaign was the targeted elimination of Iranian mobile SAM units. These units, including the domestically produced Raad and Bavar-373 systems, were suppressed through a combination of signals intelligence to locate their positions and time-sensitive strikes. Israel also appears to have used decoys and drones to stimulate Iranian radar systems into emitting, thereby revealing their locations for follow-on strikes.
Within the first 72 hours, Israel reportedly neutralized some of Iran’s long-range air defense coverage, degraded regional radar visibility, and disrupted command coherence within Iran’s Integrated Air Defense System. By combining cyber, electronic, and kinetic attacks in a synchronized campaign, Israel established localized air superiority, which enabled follow-on operations without significant resistance from Iran’s air defense forces.
After several days of sustained attacks, the Iranian military became increasingly cautious and began to suspect the extent of fifth column activity within its own territory. In response, Iranian commanders shut down several radar systems, likely as a protective measure to preserve the remaining air defense assets in case the conflict escalated further. By limiting radar emissions, Iran may have sought to prevent further detection and targeting by Israeli forces, recognizing that active radars were being rapidly located and destroyed, often with the assistance of internal sources. This shift in tactics marked a transition from a fully active defense posture to one of radar silence and survivability, prioritizing long-term endurance over immediate coverage.
“Midnight Hammer”
Deploying the B-2 Spirit, America's stealth bomber, isn’t as simple as launching a jet into the sky; rather, it’s a “logistical nightmare” involving several dozen aircraft, hundreds of personnel, and planning that stretches across continents.
The B-2’s range is impressive, over 11,000 kilometers, but to reach deep targets across the globe and return safely, it relies heavily on aerial refueling. That means KC-135 Stratotankers or KC-46 Pegasus aircraft must rendezvous with the B-2 mid-flight, often multiple times, over international airspace. These tankers themselves need support, clear flight corridors, basing agreements, and contingency planning.
Then there’s the matter of fighter escort. While the B-2 is stealthy and can often operate independently, in higher-threat zones it may be accompanied by F-22 Raptors or F-35s, which help suppress enemy air defenses, protect tankers, and secure the airspace. Coordinating these escorts adds complexity: fighters require their own refueling, communications, and threat briefings, all of which must be synchronized with the bomber’s flight plan.
Furthermore, every B-2 mission relies on secure communications, GPS accuracy, and weather data, making satellite support and real-time intelligence feeds essential. Even minor delays—like a tanker being off schedule—can jeopardize an entire mission.
In short, a single B-2 strike can involve dozens of aircraft, thousands of gallons of fuel, and days of synchronized preparation. The bomber may be stealthy, but the operation around it is massive and visible, reminding us that modern airpower is as much about logistics as it is about firepower.
During Operation Midnight Hammer on June 22, 2025, B-2 bombers reportedly launched from Whiteman Air Force Base in Missouri, flying a transatlantic route over the Atlantic Ocean and Mediterranean Sea, eventually entering Iranian airspace from the west or southwest.
This flight path passed through airspace monitored by Russian radar systems, including two advanced types theoretically capable of detecting stealth aircraft under specific conditions.
These systems, which rely on ionospheric reflection to monitor targets at vast distances, are located at Kovylkino (Mordovia) and Zeya (Amur Region).
These radars can detect large, low-observable targets, such as the B-2, when operating at specific frequencies and under favorable atmospheric conditions.
Designed primarily for ballistic missile detection, some Voronezh systems have coverage overlapping the Middle East such as Armavir (Voronezh-DM) – built specifically to monitor Middle Eastern airspace and missile launches, making it the most likely to detect U.S. bomber activity over Iran; Orsk (Voronezh-M) – though optimized for northern approaches, it might have provided fringe coverage if the B-2s penetrated northern Iranian airspace.
It is highly likely that Iranian air defense was indirectly supported by Russian tracking data, given the integrated nature of regional surveillance systems and the geopolitical context.
Before a B-2 ever appears on radar, if it does at all, seasoned observers can often sense that something is coming. Unusual patterns in tanker flights, the sudden repositioning of AWACS and EW aircraft, or a spike in encrypted radio traffic all signal the early stages of a major operation. These logistical “tells” don’t go unnoticed by foreign intelligence or military watchers.
In the hours or even days before a strike, increased support aircraft activity, subtle changes in air traffic flows, and elevated communications silence protocols among U.S. assets often betray the scale and tempo of what’s unfolding. While the B-2 itself may be virtually invisible to radar, the infrastructure required to support it leaves a footprint—one that can tip off those who know what to look for.
The US exercised a deception tactic by relocating several bombers to Guam. According to Pentagon disclosures, six B-2 bombers were deployed to Guam in the lead-up to the operation, not for strike purposes, but as a deliberate deception maneuver. This feint was designed to mislead both Iranian and Russian military intelligence, suggesting the primary threat vector would originate from the Pacific.
The strategic objective of this deception was to prompt Russian radar operators to shift the operating modes of their Voronezh and Container radar networks toward ballistic missile tracking, thereby reducing their sensitivity to low-altitude, low-observable aircraft, such as the B-2, approaching from the west.
This layered strategy, combining stealth, geographic misdirection, and electronic deception, was likely critical to ensuring the strike’s element of surprise and operational success.
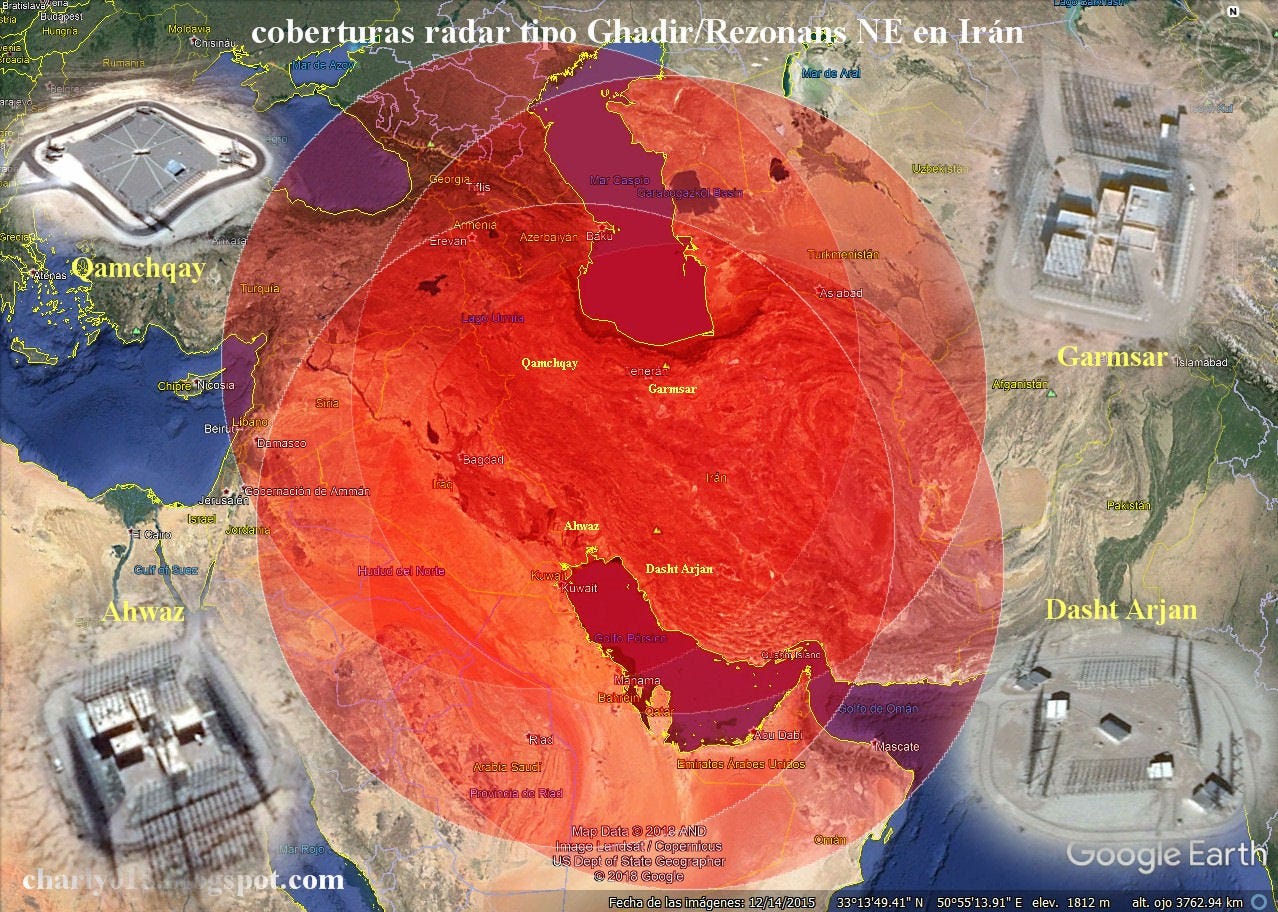
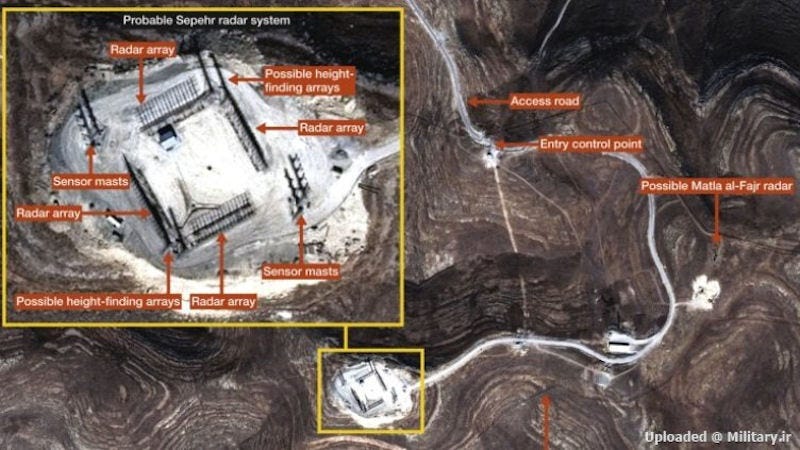
Iran has significantly bolstered its early warning capabilities through the acquisition of at least four Rezonans-N VHF over-the-horizon (OTH) backscatter radars from Russia, systems specifically designed to detect low-observable (stealth) aircraft at long range. These powerful radar stations have been locally modified to some degree and constructed in two distinct variants, forming the backbone of Iran’s long-range air surveillance network.
The larger systems, known as Sepehr, are built with quadrilateral antenna arrays approximately 100 meters across, supported by very tall transmitter towers at each corner. These elaborate, isolated installations are believed to offer deep early warning coverage, potentially monitoring aircraft and missile activity across Southwest Asia, well beyond Iran’s borders.
Complementing them are the smaller Qhadar radars, which also use a quadrilateral layout but are less than 70 meters wide and contain a central transmitter tower rather than corner-mounted ones. These stations are more modest in design, often placed in rural farmland, and appear to serve as regional or gap-filler coverage nodes.
Together, the Sepehr and Qhadar3 radars provide extensive and overlapping VHF-band surveillance coverage of Iranian airspace. Their low-frequency operation gives them an advantage in detecting stealth aircraft, such as the B-2 Spirit or F-35, which are optimized to evade higher-frequency radar bands.
However, while these radars can alert Iran to the presence of stealth aircraft, their ability to provide precise targeting information remains limited. In a modern electronic warfare environment, they are still vulnerable to jamming, cyber disruption, or decapitation strikes by long-range missiles or internal sabotage.
Nonetheless, this radar network represents a serious upgrade in Iran’s strategic situational awareness, further complicating the planning of any foreign air operations in the region.
Passive approach
Instead of emitting signals like regular radars, passive radar systems work by picking up existing radio waves (such as TV, radio, or cell phone signals) that bounce off an aircraft. These systems cannot be jammed or easily avoided. Iran is rumored to be developing such systems and could potentially use them in urban or densely populated environments. The challenge for B-2 is that its stealth is less effective against these forms of detection because passive radar doesn’t rely on bouncing signals from a central emitter.
While not primary detection tools, Iran could also use Electro-optical (EO) and infrared search and track (IRST) systems to detect the heat signature of the B-2. These are useful during clear weather, night operations, or from high-elevation areas. The B-2 is designed to have a low IR signature, but no aircraft is heat-invisible, especially during takeoff, descent, or after long missions.
Iran’s radar network is diverse but vulnerable. While it includes long-range systems like the (S)Epehr and Ghadir, as well as imported technology such as Russian VHF radars, these systems have gaps. They are less effective at detecting low-flying or stealth aircraft, but in this case, B-2 definitely didn’t fly low. In cases where the enemy has superiority in attacking means, survivability tactics such as turning radars off to avoid being targeted are often applied, but this further reduces Iran’s situational awareness. As this operation was highly likely coordinated with Israel, radar coordination across sectors may have been compromised by cyber and EW attacks.
Behind the Scenes
It’s possible that Iranian political leaders hesitated to authorize a full air defense response until the nature and scale of the attack became clear. Fear of escalation, uncertainty, or internal confusion might have led to delayed or constrained engagement orders, especially if the aircraft were already on their way out after delivering their payloads.
In the days leading up to the United States' surprise military strike on Iranian nuclear facilities on 22 June 2025, a series of clandestine diplomatic meetings were held between American and Iranian representatives in Oman. While the world focused on rising tensions and troop movements across the region, a quieter drama was unfolding behind closed doors in Muscat, where both sides engaged in last-ditch efforts to prevent a war.
According to intelligence and diplomatic sources familiar with the talks, the meetings began in early June and continued until just hours before the first wave of U.S. aircraft entered Iranian airspace. The setting was discreet—a private Omani government villa near the coast—where mid-level diplomats, intelligence officers, and back-channel envoys exchanged signals, warnings, and last-minute proposals.
Oman has long served as a trusted mediator between Washington and Tehran. In 2013, it hosted the secret nuclear negotiations that eventually led to the Joint Comprehensive Plan of Action (JCPOA). In 2025, as tensions escalated over Iran's enrichment activities, Oman was again asked to play the role of quiet facilitator.
However, unlike past negotiations, this time there was no roadmap for compromise. According to two sources with direct knowledge of the talks, the U.S. team, believed to include CIA and Pentagon liaisons, delivered a stark message: unless Iran immediately and verifiably halted advanced uranium enrichment and dismantled several underground centrifuge clusters, military action was imminent.
The Iranian response was firm but restrained. Negotiators reportedly offered a temporary suspension of enrichment at one of the key sites—possibly Fordow—in exchange for guarantees of no further sabotage or assassination attempts against Iranian scientists. Tehran also sought the release of frozen assets and the easing of sanctions on oil exports.
But for Washington, that wasn’t enough. With intelligence indicating Iran was days or weeks away from reaching weapons-grade enrichment thresholds, the Trump administration had reportedly made the strategic decision that containment was no longer viable. The talks in Oman, then, were not a platform for a deal—they were a final warning.
Omani officials, always cautious and understated, reportedly pleaded with both sides to allow more time for a diplomatic breakthrough. King Haitham's government was concerned not only about regional stability, but also about the potential civilian fallout and the possibility of Iranian retaliation across the Gulf. Despite their efforts, the tone of the meetings grew increasingly tense, and by June 20, U.S. delegates left Muscat.
Just before dawn on June 22, a coordinated strike began. U.S. B-2 bombers, F-35s, and cruise missiles targeted key elements of Iran’s nuclear infrastructure, including Natanz, Fordow, and a suspected new facility near Isfahan. Cyber operations and internal sabotage complemented the external attack.
The secret Oman talks have not been officially acknowledged by either side. Iranian state media has made no mention of the meetings, while U.S. officials have neither confirmed nor denied their existence.
When U.S. stealth bombers and cruise missiles struck Iran’s nuclear sites in the early hours of June 22, 2025, many observers were surprised by what didn’t happen: there was no immediate massive Iranian response, except the missile launch toward the US base in Qatar.
According to multiple Western and regional officials, the United States delivered a discreet warning to Tehran in the hours before the strikes. The message—relayed through a combination of Swiss diplomatic channels, Qatari intermediaries, and backchannel signals-was clear: the U.S. would strike specific nuclear targets only, and Iran should avoid escalation if it wanted to prevent a broader war.
One senior Gulf intelligence official described it as “a calibrated message—not asking for permission, but offering a limit.” The U.S. reportedly made it clear that no leadership targets, civilian infrastructure, or military barracks would be hit—only nuclear facilities deemed to be in violation of past agreements.
Iranian leaders, faced with overwhelming American air power and a deteriorating economy, made a calculated decision not to respond militarily. Sources inside Iran say elements of the air defense network were even ordered into a standby mode shortly before the strikes, not to provoke, not to expose.
In the days that followed, Iran’s official response remained restrained. There were denunciations in the media and diplomatic protests, but no serious and massive military action against the US targets, just a symbolic bite, for which they communicated the exact time of the attack to the US base in Qatar, and the base was evacuated. Instead, Iran emphasized national resilience and regional diplomacy, quietly regrouping behind the scenes: “The Art of the Deal” in practice.
So, this war chapter is over, and all three sides declared victory… Well, so be it… until the next time.
Conclusion
The B-2 Spirit remains one of the most advanced and iconic strategic bombers in the world, designed to penetrate deep into enemy airspace and deliver precision-guided munitions undetected. With its flying wing design, radar-absorbing materials, and low thermal and acoustic signatures, the B-2 can evade most conventional radar systems, especially those operating in higher frequency bands. It can carry both conventional and nuclear payloads and fly intercontinental missions with aerial refueling, making it a core asset in U.S. power projection.
But despite its reputation, the B-2 is not invincible.
This was illustrated in 1999, when Serbian air defenses using Soviet-era technology shot down an American F-117A Nighthawk, a stealth aircraft often considered even more elusive than the B-2 under certain radar profiles. The incident served as a reminder that stealth is not the same as invisibility, and adapting tactics, timing, and ground-based intelligence can challenge even the most advanced systems.
The B-2 remains a powerful tool, but in a world of evolving detection technologies, its survivability increasingly depends on the element of surprise, effective mission planning, and a favorable strategic environment.
[i] Edited by Piquet (EditPiquet@gmail.com
Bibliography
For those interested in B-2 development and combat history, as well as technical literature discussing its RCS, here are a few recommended sources:
Bill Scot: Inside the Stealth Bomber: The B-2 Story
Thomas Whittington: B-2A Spirit Units in Combat
Steve Pace: B-2 Spirit: The Most Capable War Machine on the Planet
Jay Miller: B-2 Stealth Bomber
M. Mihajlovic & Dj. Anicic: Shooting Down the Stealth Fighter
Вождаев В. В.: Характеристики радиолокационной заметности летательных аппаратов - монография
О.И. Сухаревский, В.А. Василец, С.В. Кукобко: Рассеяние электромагнитных волн воздушными и наземными радиолокационными объектами: монография
Air Force Magazine, January 2017
R. Grant: Spirit of Innovation
If you like the article (and many more articles regarding military subjects will come) you can buy me a coffee:
https://www.buymeacoffee.com/mmihajloviW
Рассеяние электромагнитных волн воздушными и наземными радиолокационными объектами: монография / О.И. Сухаревский, В.А. Василец, С.В. Кукобко и др. // Под ред. О.И. Сухаревского
https://www.airandspaceforces.com/article/1099stealth/
In some sources, Epher and Ghadir names are used. It depends on the pronunciation.













dear god, Mike, you've outdone yourself. There's nowhere else on the internet where you can find this depth and breadth of analysis drafted in a format a layperson can understand. Bravo.
Hi Mike, thanks, finally an overall approach how that war could have looked like. Much appreciated. The rugged territory of Iran is difficult for AD, as approaching aircraft can hug the valleys of Northern Zagros (coming from Iraq and/or Azerbaijan) and thus remain invisible for Iranian RADAR. No difference whether F15, F16 or F35. Except if these valleys are individually defended by SHORAD based on acoustic and visual recognition.
Iran has clear skies in mid June. And a large population equipped with smartphones. How comes, not a single picture emerged showing Israel's planes in Iranian skies? Either flying only at night, at greater altitudes [even than, videos with a dot in the sky and the typical acoustic pattern would have emerged] or didn't fly at all. Leaving the damage for standoff weapons and local cells with Spike and drones.
When it comes to "Fordo" [would be time to stop using this name as Fordo (فردو) is a village South of Qom, whereas the enterprise in question is located North of Qom, near Safarabad] within a black hill range - obviously volcanic basalt] the only evidence given are "satellite" pictures. Sun shows these pictures being taken in early morning ~6 AM local time. That would be possible if a satellite was in position, another 2 hours later the image was processed and released in a strange mix of orientations [top North, W, E, S]. Hard working people. As with many "satellite" pictures in both ongoing wars, they don't show reality but a scripted story. Rather often obviously enhanced with photoshop [BDA edition]. Sorry, but when one releases such mix of pics not in top North - it looks fishy.
So far, I don't believe B2 had entered Iranian air space. These 3 sites may have been attacked from B2 using cruise missiles. There is absolutely no reason for Iran to belief assurances by the US in terms of limited strikes. I remain skeptical on these back door agreements.